Noosc Attack Vector Testing
Attack vector testing involves identifying and evaluating the various paths or means.
Our Services
Attack Vector Testing
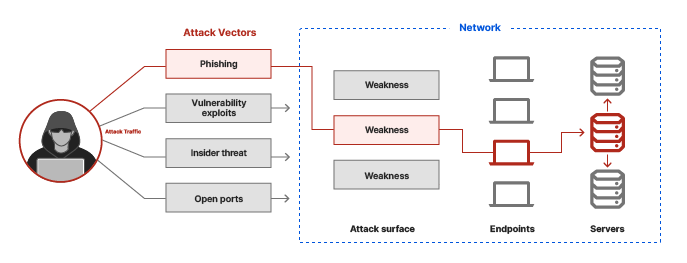
Attack vector testing involves identifying and evaluating the various paths or means through which an attacker might exploit vulnerabilities to gain unauthorized access to a system or network. Here are some key components and steps involved in attack vector testing:
- Identify Assets: List all critical assets such as servers, databases, applications, and networks that need protection.
- Map Attack Surfaces: Determine all possible points where an attacker could attempt to gain access. This includes physical access points, network interfaces, and software applications.
- Threat Modeling: Create models to understand potential threats and how they might exploit vulnerabilities. This includes identifying potential attackers, their goals, and the tactics they might use.
- Vulnerability Assessment: Scan systems and networks for known vulnerabilities. This can be done using automated tools like Nessus, OpenVAS, or manual testing.
- Penetration Testing: Simulate attacks to identify weaknesses in a controlled manner. This involves using techniques like social engineering, phishing, or exploiting software vulnerabilities.
- Red Teaming: Engage a group of security professionals to perform full-scale attacks to test the effectiveness of the organization’s security measures and response capabilities.
- Review and Remediate: Analyze the results of the testing to identify security gaps and take corrective actions to mitigate identified risks.
- Continuous Monitoring: Implement ongoing monitoring and regular testing to ensure that new vulnerabilities are detected and addressed promptly.
We use several methodologies used in attack vector testing, each with its specific focus and approach, like:
- OWASP Testing Guide
- NIST SP 800-115
- PTES (Penetration Testing Execution Standard)
- OSSTMM (Open Source Security Testing Methodology Manual), etc
- etc
Each of these methodologies provides a structured approach to identify, assess, and mitigate security risks. The choice of methodology depends on the specific requirements, scope, and goals of the attack vector testing project.